14) which of the following are breach prevention best practices
Access only the minimum amount of PHIpersonally identifiable information PII necessary. Best Practices for Preventing Data Breaches.

How Security Awareness Can Help Prevent Insider Threats
Reduce the level of employee negligence.

. Organizational leaders know this. Logoff or lock your workstation when it is unattended. Implement a documented system for departing employees and vendorscontractors passwords key cards laptop access etc Train employees on the importance of reporting suspicious data security leakage or data security breaches.
Containment eradication and recovery. While the causes of breaches may vary the effects are very similar across the board. Published Jul 14.
True False 14 Which of the following are breach prevention best practices. These 15 best practices can be used to reduce the likelihood of a data breach and help you respond more quickly to an attack. Heres our IT security best practices checklist that you can rely on to find answers to these questions and prevent cyber attacks.
A breach can be the result of internal or external attackers. Employee Training and Awareness. Encryption can be software-based or hardware-based.
These practical user-friendly guides can help your practice facilitate the adoption of standards-based approaches to cybersecurity. Learn from Experian data breach best practices in healthcare data breach resolution. Cloud and Hybrid.
A journey map Document Published Date. Published Jul 14 2022 In our latest fraud infographic we map out a consumer journey that ties together seamless recognition with fraud prevention so businesses can provide an enhanced customer experience while properly treating third-party first-party and synthetic. Remediation Accessed N PHI transmitted orally PHI on paper PHI transmitted electronically correct All of the above-----11 Which of the following are breach prevention best practices.
Compliance required by 92314 New BAAs executedrenewed after 12513 Must conform to new rules. The following are breach prevention best practices. Loss of customer trust brand damage reputational harm legal exposure and higher costs.
Breach Notification Rule - 45 CFR 164400-414 If an impermissible use of disclosure of PHI is determined to be a Breach CEs must provide notification of the Breach to affected individuals the Secretary of HHS The Secretary state entities under applicable state law and in certain circumstances to the media Reputation. Data encryption is an often overlooked data security best practice but its incredibly effective because it makes stolen data useless to thieves. Access only the minimum amount of PHIpersonally identifiable information PII necessary.
Create a policy that describes how employees should handle dispose of retrieve and send data. Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your workstation when it is unattended Promptly retrieve documents containing PHIPHI from the printer All of this above 15 An incidental use or disclosure is not a. You must know what sensitive information you have collected stored transmitted or processed before you.
System and data users are the weakest link in the implemented cybersecurity programs and the most vulnerable to data breach attacks. Addresses three types of safeguards - administrative technical and physical - that must be in place to. We map out a consumer journey that ties together seamless recognition with fraud prevention so businesses can provide an enhanced customer experience while properly treating third-party first-party.
Following this sheet is the Summary and Next Steps sheet a. The Five Most Frequently Asked Questions About Data Breach Recovery. Top 15 cybersecurity best practices.
The CERT Insider Threat Center at Carnegie Mellon University is one of the worlds leading authorities on detecting insider fraud and it has just released Version 6 of its Best Practices to Mitigating Insider Threats. As part of this research the center addresses how to detect and prevent insider fraud as well as how to map insider threat. The following methods describe the best way a business owner can prevent data breaches in their companies.
1800-3 Attribute Based Access Control. Protects electronic PHI ePHI c. The publications with specific applicability to healthcare are.
Employ a people-centric security approach. Best Practices in Breach Prevention - Minimizing the Risk of a Breach. It describes a process and its elements for the treatment of.
1800-4 Mobile Device Security. Promptly retrieve documents containing PHIPHI from the printer. 10 The HIPAA Security Rule applies to which of the following.
This paper focuses solely on the aspects of re-establishing best practices safety. Public Health Nigeria Public Health Nigeria an Interdisciplinary public health movement focused on health education advancing fair public health policies promoting fitness healthy diets responsible behavior community health and general wellbeing. Sensitive data about identity collected stored transmitted or processed.
Established a national set of standards for the protection of PHI that is created received maintained or transmitted in electronic media by a HIPAA covered entity CE or business associate BA b. 1800-1 Securing Electronic Health Records on Mobile Devices.

6 Things You Need To Do To Prevent Getting Hacked Wired

Data Breach Vs Data Leak What S The Difference Upguard
How To Secure Your Phone 20 Ways To Improve Mobile Device Security The Missing Report

Data Breach Vs Data Leak What S The Difference Upguard
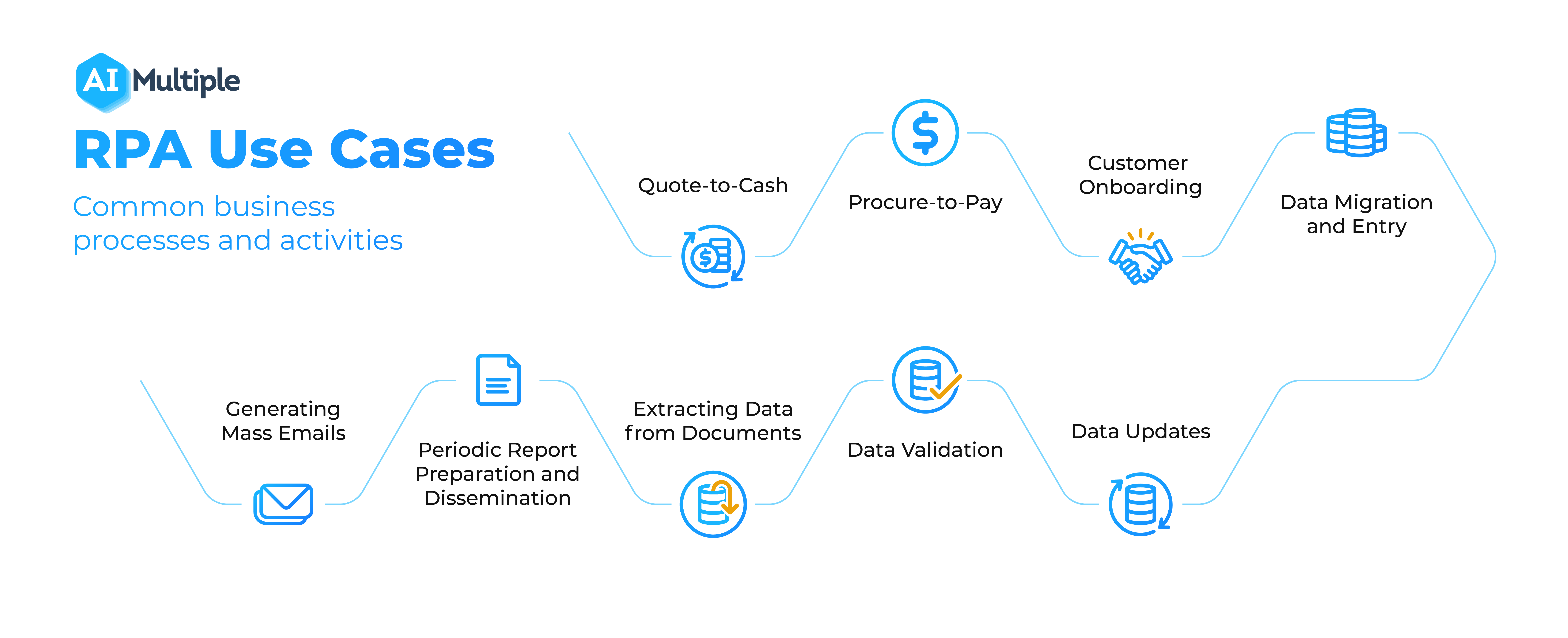
Top 65 Rpa Use Cases Projects Applications Examples In 2022

Top 20 Docker Security Best Practices Ultimate Guide

Aws Cloudformation Security 8 Best Practices Cycode

Privacy Security Blog By Prof Daniel Solove Teachprivacy Training

Official 2022 Hipaa Compliance Checklist

Top 20 Docker Security Best Practices Ultimate Guide

Privacy Security Blog By Prof Daniel Solove Teachprivacy Training

Official 2022 Hipaa Compliance Checklist

4 Most Common Causes Of Data Leaks In 2021 Reciprocity

15 Alarming Cyber Security Facts And Stats Cybint

Data Breach Vs Data Leak What S The Difference Upguard

Privacy Security Blog By Prof Daniel Solove Teachprivacy Training